Managing secrets in asp.net core web applications part 1 : How to store secrets for local development
Secret management is a well know topic and all the frameworks have their own strategy on how to deal with application secrets in a secure manner.
The problem we need to solve with user secrets is how do we make sure that these secrets are not available to the outside world as part of our code. So basically we want our secret configuration to be separate from our code. And this applies both to our local development environment and production environments.
Usually, developers would add a secret e.g. database connection string with a password in the application configuration file (e.g. web.config or appsettings.json ). These secrets are then part of source control and are available to anybody who has access to code.
In this post, we will discuss how to manage secrets correctly in an asp.net core application both during local development (part 1) and after deployment (part 2).
Managing secrets
For local development, we can use a feature called user secrets. The feature is part of asp.net core secret manager tool which can be accessed through visual studio or command-line interface (CLI).
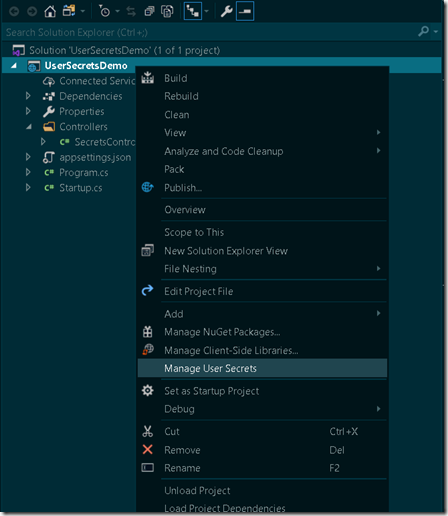
To enable user secrets via visual studio we can right-click the project file and click ‘Manage user secrets’ option.
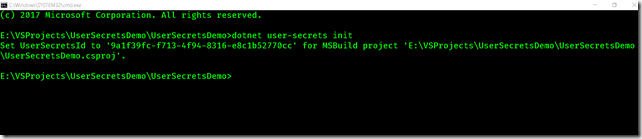
or we can also do it using command line using the command
dotnet user-secrets init
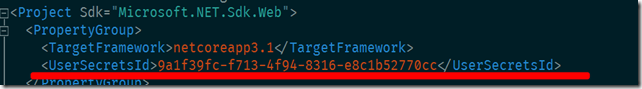
Executing any of these options generate a unique key (a guid) in the project file.
Now you can add your secrets to project either using the command line or directly to secrets.json file by clicking on manage user secrets option shown earlier.
The thing to note here is that you never should / have to access the secrets.json file directly from its location. Location and managing this file is abstracted through secret manage tool and you don’t have to worry about it. Usually, on windows, this is stored somewhere in the user profile folder separate from project structure and is never part of source control.
Adding secrets
Adding secrets through command line we can use ‘dotnet user-secrets set’ command e.g.
dotnet user-secrets set “Keys:Primary” "Primary key"
dotnet user-secrets set “Keys:Secondary” “Secondary key”
dotnet user-secrets set “ConnectionString” “A secret connection string”
dotnet user-secrets set “AnotherKey” “Another secret key”
As seen above you can add both plane key-value or hierarchical (using colon) key values.
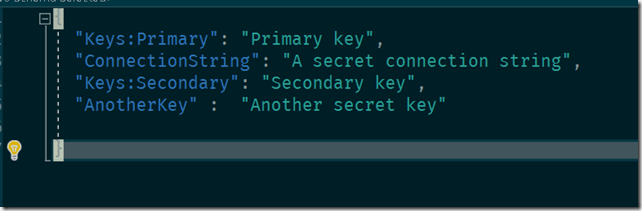
This is how our secrets file looks like after this.
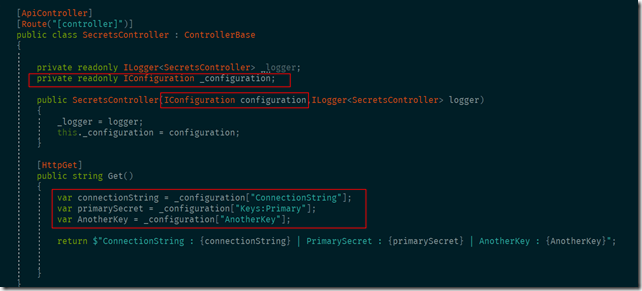
Accessing secrets
This is really the simple part. All the user secrets added above can be accessed using the configuration class. This is also one of the important concepts in asp.net core where we have different sources which can act as configuration provider (e.g. JSON files, environment variables, azure key vault etc) and all of them can be accessed in the same manner from code as shown below.
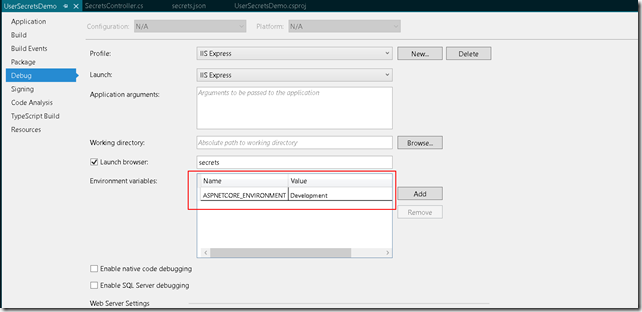
An important point to note is that user secrets values are only available on development environment i.e. when the value of ASPNETCORE_ENVIRONMENT variable is ‘Development’.This is the default when you do local development using visual studio.
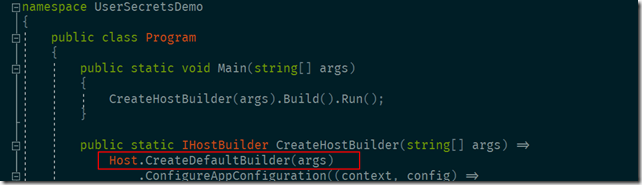
If you are using the default implementation of asp.net core project and in Program.cs file calling Host.CreateDefaultBuilder than you don’t have to do anything specific to have user secrets as part of your configuration source but if you have customized this code then you need to call AddUserSecrets() method on the configuration object in your program.cs file wherever you are configuring you app configuration.I’ll show you this in my next post where we do something similar for Azure key vault.
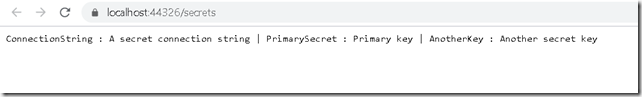
If you run this application and call the endpoint which returns all the configuration values you would see something like this.
Just out of curiosity try changing the ASPNETCORE_ENVIRONMENT to something else e.g. Production and run the application. None of the configurations would be fetched.
And that would be topic of my next post i.e. how to use azure key vault to access user secrets on production / non-local environments.
To get more details on this topic you can refer to this excellent short course by Matt tester on pluralsight. It’s a must-have if you want to fully understand this topic.
Pingback: Managing secrets in asp.net core web applications part 2 : How to store secrets on production environment | Coding Canvas